Updating cached password over VPNs
ADSelfService Plus can update local cached credentials stored in users’ machines so remote users can access their machines even if they forget their passwords.
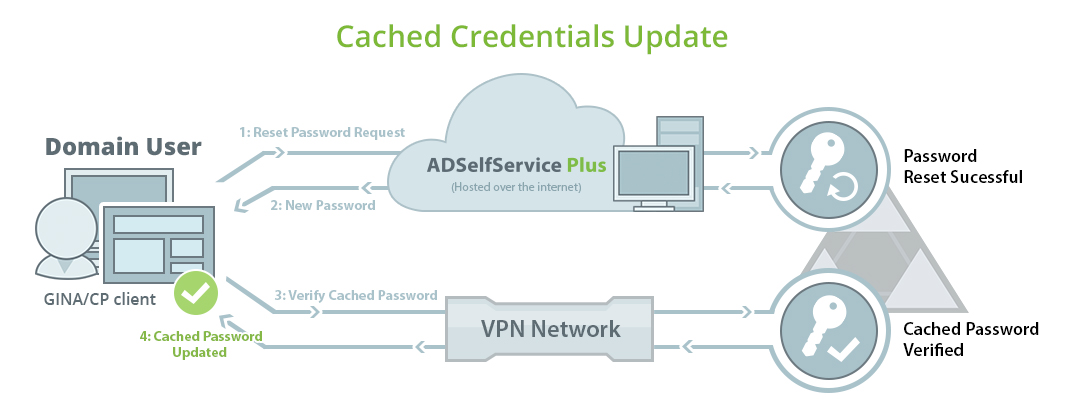
Fig 1: Image showing how a cached credential is updated by the login agent.
- ADSelfService Plus places a Reset Password/Account Unlock link on the login screen of Windows, macOS, and Linux machines to enable self-service password reset. Clicking this link will open the password self-service portal.
- Users are required to prove their identity through any one of the enforced authentication methods, such as SMS-based one-time passwords (OTPs), email-based OTPs, Google Authenticator, Duo Security, and RSA SecurID.
Important:
- Updating cached credentials over VPNs is supported only for Windows.
- Users must be enrolled in ADSelfService Plus to utilize the self-service password reset and self-service account unlock capabilities.
- Enrollment is a one-time process where users enter their mobile number and email address, set answers to security questions, and provide other details in ADSelfService Plus in order to register for self-service password management. Learn how to enroll users.
- Once a user’s identity is successfully verified, they will be allowed to reset their forgotten AD domain passwords.
- ADSelfService Plus resets the AD password and alerts the logon agent about the successful completion.
- The logon agent establishes a secure connection with AD through a VPN client and initiates a request for updating the local cached credentials.
- After the request is successfully approved by AD, the cached credentials are locally updated on the user's machine.
Supported VPN clients
- Fortinet
- Cisco IPSec
- Cisco AnyConnect
- Windows Native VPN
- SonicWall NetExtender
- Checkpoint EndPoint Connect
- SonicWall Global VPN
- OpenVPN
- Custom VPN
Note: The ADSelfService Plus login agent uses a command-line interface (CLI) to initiate a connection with the integrated VPN. Any VPN provider that supports a CLI with LocalSystem account privileges can be used for cached credentials update.
Configuration Steps
- Navigate to Configuration → Administrative Tools → GINA/Mac/Linux (Ctrl+Alt+Del).
- Click Updating Cached Credentials over VPN.
- Select Enable VPN settings.
- Select the VPN Provider from the drop-down list.
- Enter the VPN Hostname/IP address and VPN Port No in their respective fields.
- Enter the location where the VPN client is installed on the users' machines.
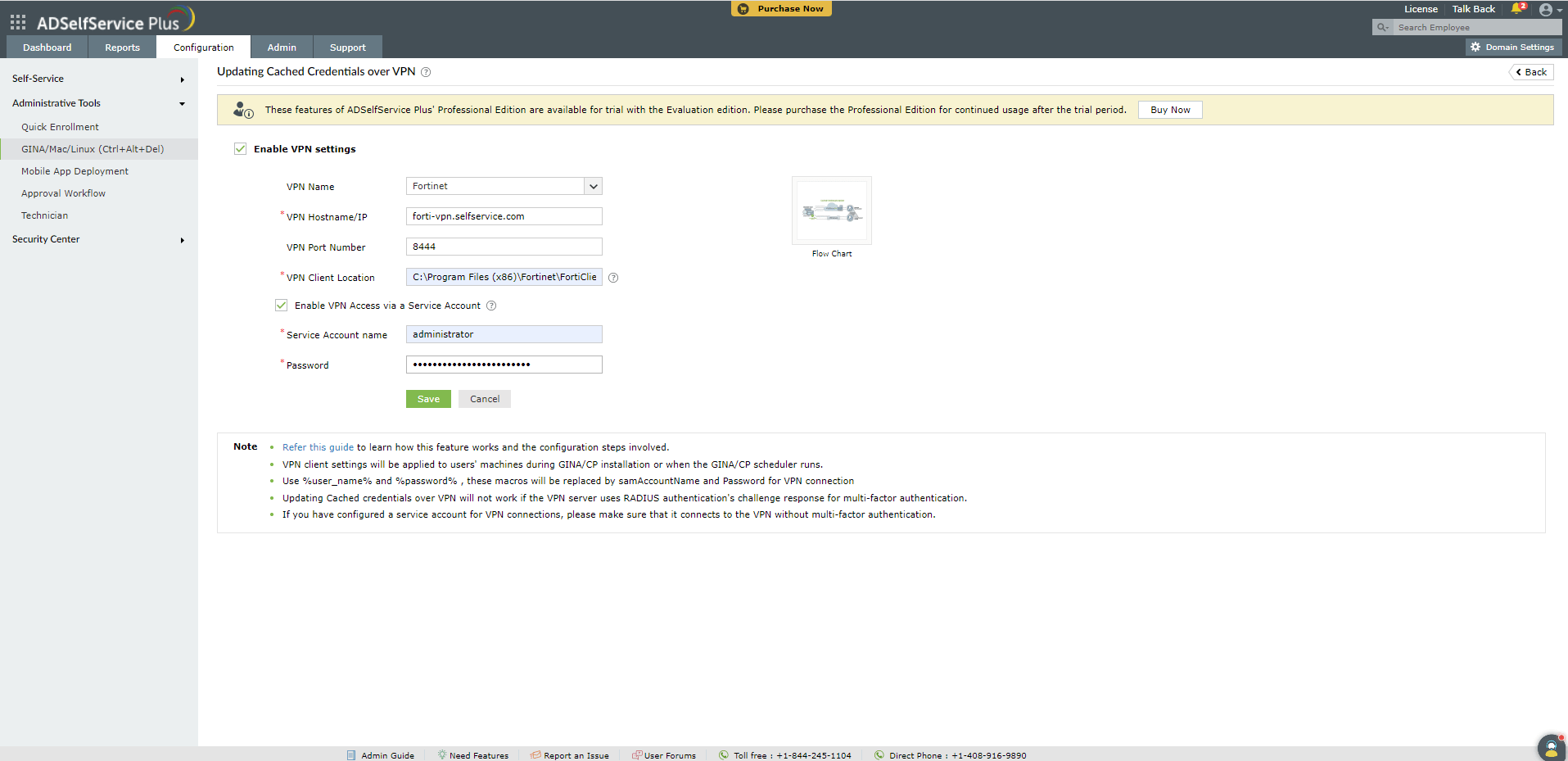
- If you want to use a service account for VPN connections, select Enable VPN Access via a Service Account and enter the service acount's credentials.
Note: VPN connections are usually made with end-user accounts. You can use a service account for VPN connections if:
- Your organization has mandated MFA for end-user VPN connections, or
- Your organization uses a single account for multiple VPN connections.
Please ensure that the VPN service account does not require MFA in order to connect to the VPN.
Here are the client locations for the VPN providers supported out of the box in ADSelfService Plus:
- Cisco AnyConnect: C:\Program Files (x86)\Cisco\Cisco AnyConnect\vpncli.exe
- SonicWall Global VPN: C:\Program Files (x86)\SonicWall\SonicWall Global VPN\swgvc.exe
- Fortinet VPN: The appropriate version of the VPN client file (fortisslvpnclient.exe) must be downloaded from the Fortinet support portal and installed on users' machines. The location where the FortiSSLVPNClient.exe file has been installed must be mentioned as the client location. Example: C:\FortiClient\FortiSSLVPN\x86\FortiSSLVPNClient.exe
- Check Point VPN: C:\Program Files (x86)\CheckPoint\Endpoint Connect\trac.exe
- SonicWall NetExtender: C:\Program Files (x86)\Sonicwall\SSL-VPN\NetExtender\necli.exe
- OpenVPN: C:\Program Files (x86)\Sophos\Sophos ssl client\bin\openvpn.exe
- Cisco IPSec: C:\Program Files (x86)\Cisco\Cisco IPSec\vpnclient.exe
Note: The VPN client location has to be uniformly maintained on all user machines. If using a custom VPN provider, please contact your VPN provider's support team to know the name of the client used for command-line interface and mention its location as the client location.
- For Custom VPN, macros (%user_name%, %password%, etc.) can be used in the VPN Connect/Disconnect Command. (Note: The syntax for the VPN Connect/Disconnect Command varies depending on the VPN provider used.)
Example:connect -s adsspvpn -h %servername%:%portno% -u %user_name%:%password%
- Click Save.
Note:The VPN configurations will be reflected on the users’ machine either during the GINA/Mac/Linux client installation, or when the GINA/Mac/Linux scheduler runs.
Don't see what you're looking for?
-
Visit our community
Post your questions in the forum.
-
Request additional resources
Send us your requirements.
-
Need implementation assistance?
Try onboarding